Answers: ACL Drill Set 1
Today’s post lists the answers to ACL drill set 1. What’s that? Check out this post that explains the details. No stopwatch, no speed requirement for these, unlike the subnetting speed practice. Answers are below the fold!
First, use this figure as the backdrop:
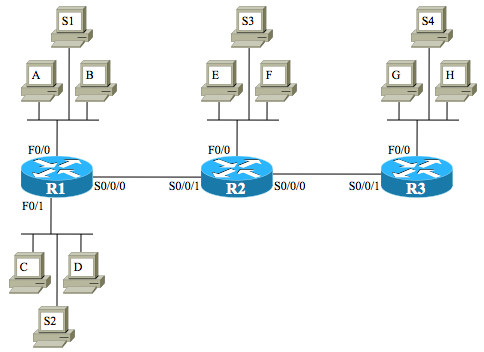
Next, I’ve left the problem statements for easier reference, with the answer to follow each:
1) Host A (10.1.1.1/24) attempts to connect to Telnet server S3 (192.168.2.254/27). Your ACL will be applied outbound on R1’s S0/0/0 interface. Permit traffic from host A to telnet services on S3, as well as telnet services on all servers in that same subnet.
permit tcp host 10.1.1.1 192.168.2.224 0.0.0.31 eq telnet
2) Host C (10.1.101.145/22) attempts to connect to web server S4 (192.168.3.250/28). Your ACL will be applied outbound on R3’s F0/0 interface. Deny hosts in host C’s subnet from communicating with web services on web server S4.
deny tcp 10.1.100.0 0.0.3.255 host 192.168.3.250 eq www
(Note: I’m looking for one statement to match what’s listed. You can assume the implied deny all at the end of the ACL, or an explicit permit all at the end; the focus is on getting this one command to match exactly.)
3) Repeat #2, but for an ACL that will be placed on R1’s F0/1 as an outbound ACL.
deny tcp host 192.168.3.250 eq www 10.1.100.0 0.0.3.255
(Note: this one just reverses the source and destination parts of the matching logic compared to #2.)

Hello Wendell
I was wondering whether using a host’s IP address + wildcard mask instead the host subnet’s Subnet ID + wildcard mask (when one means the whole subnet) is considered as correct in the exams when issuing these ACL commands. I am aware of the fact that IOS automatically corrects my command should I use the host’s IP address but I keep wondering if this practice will cost me points in the exam.
Thanks in advance
Actually, #3 could be configured as “deny tcp host 192.168.3.250 eq www any”, since outgoing F0/1 interface, only C’s subnet exists.
Hi Pedro,
I agree, that would work as well.
Wendell
Hi Wendell,
Although not mentioned here I assume it would be acceptable to use the well known port number instead of the well known service name?
e.g. deny tcp 10.1.100.0 0.0.3.255 host 192.168.3.250 eq 80
Hi Bav,
I’m good with it! IOS will change it to the service name, but for real life, I’m good either way.
Wendell
Hi Wendell,
In question #3, the config is reversed. Why that way as opposed to writing it out as “ip access-list xxx deny tcp 10.1.100.0 0.0.3.255 host 192.168.3.250 eq 80?”
Asia,
Because of the direction of the ACL. The ACL for #3 is outbound on R1’s F0/1, so the traffic is going TO host C (subnet 10.1.100.0/22), not from it. So the matching of the destination subnet has to list 10.1.100.0 0.0.3.255. Similar reason for listing server S4 as source, because of the direction.
Does it mean that the trafic from host C will leave R1 and reach S4 then come back but in this point acl on R1 will block it ??
Marcin,
To one level of depth of thinking, the short answer is yes. To a level deeper, the answer is no. That is…
TheACL does not examine packets sent from host C to reach S4. Those packets reach S4, and then S4 generates new/different packets in reply. Those will flow back to host C. Those packets will exit R1’s F0/1, which will cause R1 to process the ACL.
Thank you !